Secure Storage Service
- Author:
- Giordano Scuderi
- and
- Diego Scardaci, Nicola Dominante
The Secure Storage service for the gLite middleware provides users with a set of tools to store in a secure way and in an encrypted format confidential data (e.g. medical or financial data) on the grid storage elements. The data stored though provided tools will be accessible and readable by authorized users only. Moreover, it solves the insider abuse problem preventing also the administrators of the storage elements to access the confidential data in a clear format. The service has been designed and developed for the grid middleware of the EGEE Project, gLite, in the context of the TriGrid VL Project.
Secure Storage documentation generated with Doxygen are available.
It is composed by few component (shown below in Fig. 1):
- Secure Storage Framework
- Keystore Service
- Keystore client API
- Lcg-like API
- Posix-like API
- CLI Programs
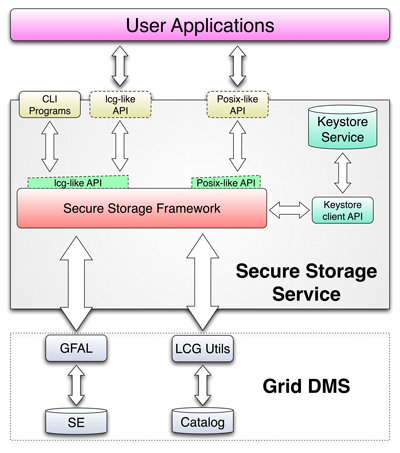
Fig. 1
Both CLI Commands and API use Environment Variables to know the Keystore hostname, port and DN.- For example:
export SS_GRID_KEYSTORE_HOST=keystore-hostname.domain.org:25406export SS_GRID_KEYSTORE_DN="/C=NATION/O=ISSUER/OU=Host/L=<RA Name>/CN=<FQDN>"
Secure Storage Framework
Secure Storage Framework: is the core of the Secure Storage Service, a unix library (both archive and shared) that contains encryption/decryption functions, and other functions necessary both to API (Lcg-like and Posix-like) and CLI Programs. This framework take care of interaction with Grid Data Management System (LFC Catalog and Grid Storage Elements).Keystore Service
Keystore Service: is a new grid element used to store and retrieve the users key in a secure way. It is identified by a host X.509 digital certificate and all its Grid transactions are mutually authenticated and encrypted as required by the Grid Security Infrastructure (GSI) model.Keystore client API
Keystore client API: used internally from API (lcg-like and posix-like) and CLI Programs, it manage the communications with Keystore, implementing a set of functions: saving, retrieving and deleting KEY and IV to/from Keystore.ss_send_key function
On new file creation, the ss_send_key function send SAVE command to Keystore.- Function prototype:
int ss_send_key(const char *lfn, const unsigned char *key, const unsigned char *iv);

Fig. 2
- Fig. 2 shows you what
ss_send_keyfunction do:- Open the connection with Keystore.
- Send SAVE command with request data (LFN, KEY and IV).
- Wait Keystore response: ACK or ERROR.
- Close connection with Keystore.
ss_get_key function
During file reading, the ss_get_key function send GET command to Keystore.- Function prototype:
int ss_get_key(const char *lfn, unsigned char *key, unsigned char *iv);
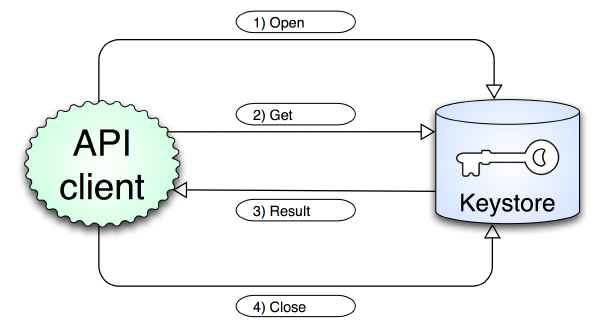
Fig. 3
- Fig. 3 shows you what
ss_get_keyfunction do:- Open the connection with Keystore.
- Send GET command with requested parameters (LFN).
- Wait Keystore response: ACK (in that case KEY and IV are returned) or ERROR.
- Close connection with Keystore.
ss_delete_key function
During file deletion, the ss_delete_key function send DELETE command to Keystore.- Function prototype:
int ss_delete_key(const char *lfn);
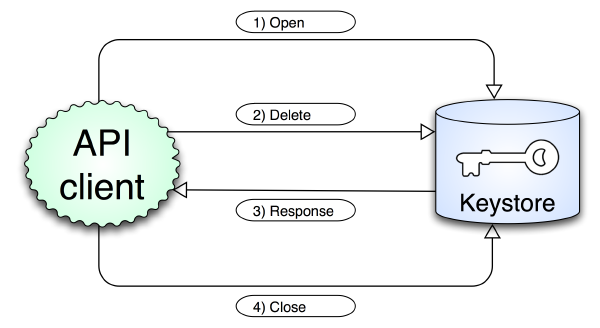
Fig. 4
- Fig. 4 shows you what
ss_delete_keyfunction do:- Open the connection with Keystore.
- Send DELETE command with requested parameters (LFN).
- Wait Keystore response: ACK or ERROR.
- Close connection with Keystore.
lcg_util-like API: Read/Write entire file
This functions behaves like Command Line Applications, they are the secure version of the lcg-utils API.These are the main functions of the Secure Storage API:
- lcg_scr
- lcg_scp
- lcg_sdel
lcg_scr function - lcg secure copy and register
Encrypt and upload a file to Grid and register it on LFC Catalog, file are encrypted in a transparent way (secure version of the lcg_cr function).- Function prototype:
int lcg_scr(char *src_file,char *dest_file,char *guid,char *lfn,char *vo, char *conf_file,int insecure,int verbose,char *actual_gid);
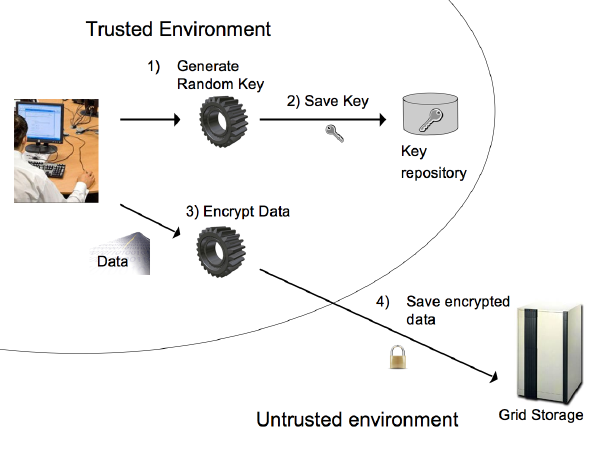
Fig. 5
- Fig. 5 shows you what
lcg_scrfunction do:- A new random secret key is generated.
- The key and the ACL are saved on the keystore.
- The input file is encrypted inside user trusted environment.
- The encrypted file is uploaded on the Grid Storage Element.
lcg_scp function - lcg secure copy
Download a file from Grid and decrypt it, file are decypted in a transparent way (secure version of the lcg_cp function).- Function prototype:
int lcg_scp(char *src_file,char *dest_file,char *vo,char *conf_file, int insecure,int verbose);
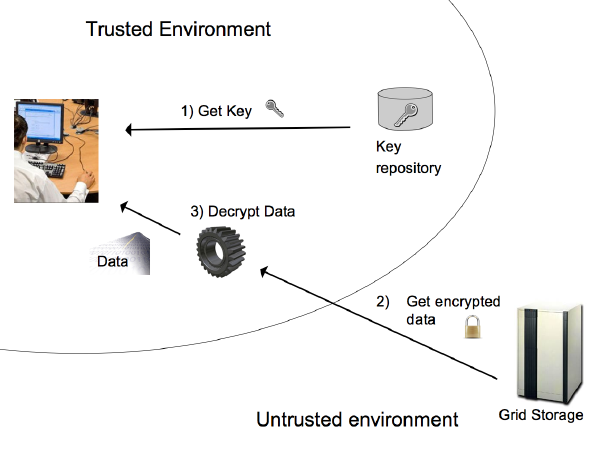
Fig. 6
- Fig. 6 shows you what
lcg_scpfunction do:- Get the secret key from the keystore: this operation fails if the user is not authorized.
- Download the encrypted file on the local machine.
- Decrypt the file and save it on the local file-system.
lcg_sdel function - lcg secure delete
Delete a file from Grid, associated KEY and IV are deleted if necessary (secure version of the lcg_del function).- Function prototype:
int lcg_sdel(char *src_file,int aflag,char *se,char *vo,char *conf_file, int insecure,int verbose,int timeout);
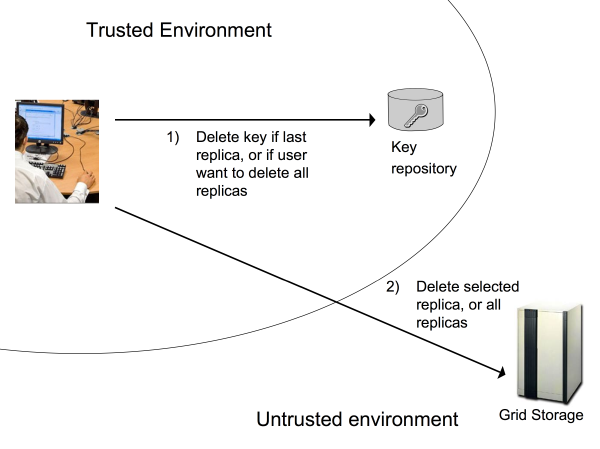
Fig. 7
- Fig. 7 shows you what
lcg_sdelfunction do:- Delete the selected file.
- Delete the secret key from the keystore if necessary: this operation fails if the user is not authorized.
Posix-like API: Read/Write block of data
The Posix-like API allows the developer to write programs able to manage encrypted remote files as local files. These functions allow developers to read or write encrypted file blocks stored on a remote storage elements in a simple way. The functions hide the complexity of working with encrypted remote files. In this way, users can manage remote encrypted files as they were clear local files.- They are the secure version of the GFAL API:
int securestorage_open( char *lfn, int flags, mode_t mode );
int securestorage_write ( int fd, void *buffer, size_t size );
int securestorage_read ( int fd, void *buffer, size_t size );
int securestorage_close ( int fd );
off_t securestorage_lseek (int fd, off_t offset, int whence);
const char *securestorage_error(int errnum);
ss_DIR *securestorage_opendir (const char *name);
struct dirent *securestorage_readdir (ss_DIR *dp);
int securestorage_closedir (ss_DIR *dp);
int securestorage_mkdir (const char *path, mode_t mode);
int securestorage_rmdir (const char *path);
int securestorage_statg (const char *path, const char *guid, struct ss_filestatg *statbuf);
CLI Programs
Command Line Application Programs: commands integrated in the gLite User Interface to encrypt and upload, decrypt and download files on the storage elements.
lcg-scr command - lcg secure copy and register
Encrypt and upload a file to Grid and register it on LFC Catalog, file are encrypted in a transparent way (secure version of the lcg-cr command).
lcg-scp command - lcg secure copy
Download a file from Grid and decrypt it, file are decypted in a transparent way (secure version of the lcg-cp command).
lcg-sdel command - lcg secure delete
Delete a file from Grid, associated KEY and IV are deleted if necessary (secure version of the lcg-del command).

